21/08/2018
In the first two months of 2018 alone there were more Cybersecurity incidents than in all of 2014. 2017 was the year in which Spain recorded the most cyberattacks since data has been available, nearly 135,000. According to data from the National Institute of Cybersecurity (INCIBE), the number of attacks was 115,000 in 2016, 50,000 in 2015 and 18,000 in 2014.
The data leave no room for doubt: cyber-attacks are on the rise. Most have been network scanning attempts or malware attacks to damage computer equipment, but it is not only large companies that are targeted. We are all exposed to increasingly sophisticated and frequent attacks that jeopardize our business, reputation, privacy and trust.
Contrary to what one might think, companies are not always attacked to obtain confidential information or «spy» on their business. The most important source of security breaches is the so-called insider threat, in which a person with legitimate access to information, whether through carelessness, negligence or malice, abuses that legitimate access and generates the security breach.
Simple examples of this could be the sending of confidential documents to a personal email account to work from home, or the employee who decides to copy company information before leaving the company, or even the one who publishes some information out of spite, using some method of anonymity.
When an attack occurs, we are not only talking about economic damage, but also about reputational damage -when it affects the trust that the environment has in the company-, or other intangible values, such as competitive advantage or intellectual property.
There is no such thing as 100% security. If we accept that, sooner or later, we will have a breach in our security, the best approach is to develop cyber resilience, defined as the ability to return to a normal state of operations in the event of an attack or incident.
So what to do at a time when cyberthreats are growing and the number of devices that can be attacked is multiplying? Let’s not forget that apps are often the entry point for attackers and present many vulnerabilities. It is certainly not a simple answer, but we can at least provide some very simple guidelines to try to strengthen cybersecurity.
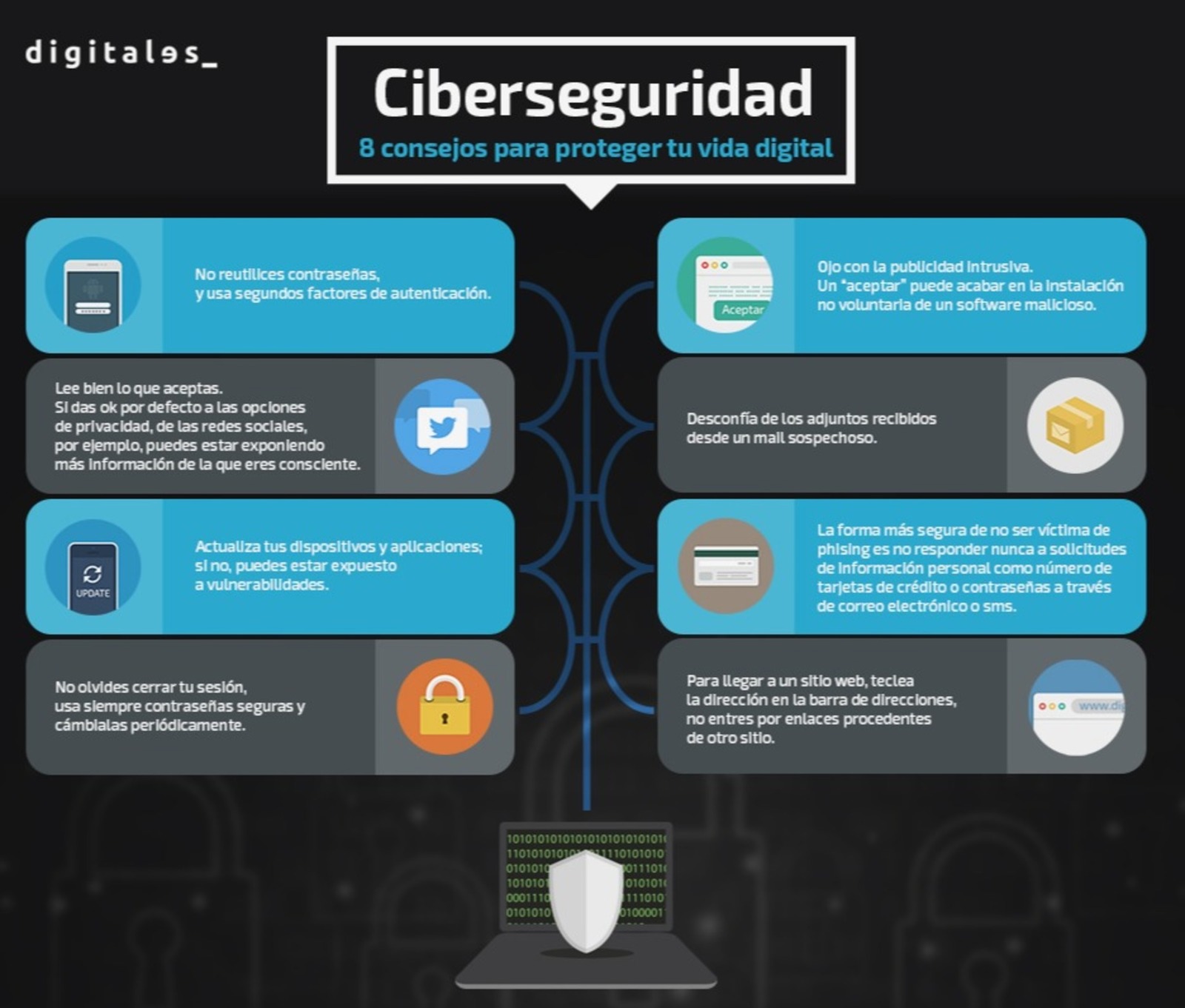
Some simple tips to protect yourself:
– Do not reuse passwords, and use second authentication factors.
– Read carefully what you agree to. If you give ok by default to the privacy options, for example, of social networks, you may be exposing more information than you are aware of.
– Update your devices and applications; otherwise, you may be exposed to vulnerabilities.
– Don’t forget to log out, always use strong passwords and change them periodically.
– Beware of intrusive advertising. An «accept» may result in the unintentional installation of malicious software.
– Along the same lines, be careful with e-mail attachments.
– The safest way to avoid being a victim of phishing is to never respond to requests for personal information such as credit card numbers or your passwords via email or sms. Entities or organizations do not request this type of data in this way.
– To reach a website, type the address in the address bar, do not enter through links coming from another site.